Software and algorithms to defend against
Jamming and
Wireless Interference
What is Jamming?
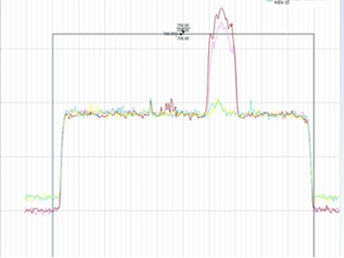
Jamming is a form of cyberattack that disrupts or blocks wireless communication. The simplest, and most prevalent, mode of jamming is to broadcast a high-powered wireless signal that drowns out the signal of interest. Any wireless network – including 5G, GPS/GNSS, LMR, and Wi-Fi – can be jammed. When user devices are targeted, only those users are affected, but when the wireless networks are targeted, the entire coverage area and many users can be compromised. Jamming is often malicious, introduced by bad actors with criminal intent.
Sources of Interference
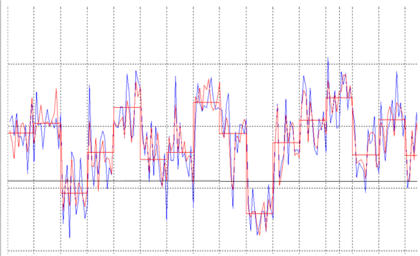
A jamming device creates RF interference for wireless networks, and in the wider context of interference sources, is just one specific type. TV broadcast towers, faulty electrical/industrial equipment, and other wireless networks also cause interference – although their operation is legitimate and the interference is unintentional. These sources are usually persistent and will continue over a long period of time. Regardless of intent, both jamming and unintentional interference jeopardize communication not only for civilians, but also for first responders, public safety, and national defense/ homeland security for whom wireless communications is mission-critical.
Protecting 5G networks
A range of interference mitigation and cancellation techniques are used to combat and defend against different jamming and interference sources and scenarios. Intentional and malicious jamming is illegal, but unfortunately growing in occurrence and becoming all too common. ISCO’s mission is to defend 5G networks, public or private, against jamming and other forms of RF interference.

Anti-Jamming: When jamming crosses borders

A jammer was used by authorities in Mexico to block cell phone usage by inmates in a prison. Being located close to the US border, the jamming signal escaped from the confines of the prison (while guards, walls, and barbed wire may confine inmates, they are ineffective against RF signals) and severely affected the operations of mobile network operators (MNO) on the American side of the border.
With the help of national regulatory bodies, the jammer's transmit power was reduced. However, this did not resolve the issue and the US MNOs still suffered from performance degradation at many cell sites. A technical solution was required.
ISCO's solution was deployed, significantly improving performance metrics including the number of connected users, downlink speed, and throughput by over 100%.
ISCO in the news
For the fourth time, ISCO has ranked in the Top 10 on Crain's list of Chicago's Most Innovative Companies based on patent awards.
Licensing ISCO patents and technology
Our algorithms and software can be embedded into RAN equipment for public or private 5G networks to counter cyberattacks and other undesirable interference.
Integrating with O-RAN
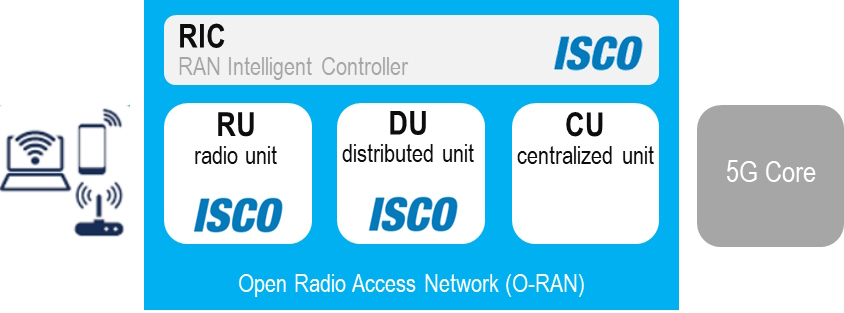
ISCO's algorithms can be embedded in the RU, DU, or RIC.
Techniques to defend against jamming and interference
PIM caused by Physical, Environmental and Spectrum Conditions
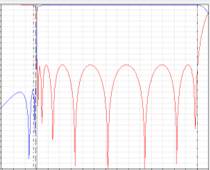
Signals from multiple transmitters can interact and create Passive Intermodulation (PIM) that degrades the uplink signal, coverage and overall network performance. The PIM problem is growing as networks evolve with more frequency bands being deployed. Our solution removes PIM, regardless of its source.
Defense and Public Safety

According to a Department of Homeland Security (DHS) survey of 4,933 first responders, 9% report that frequency interference affects their ability to communicate to a great extent, and 22% to some extent.
In this white paper, industry analysts Frost & Sullivan examines the opportunities and challenges of deploying private 5G networks in the defense and public safety sectors - with a focus on radio frequency (RF) issues.